Hazy Hawk Exploits DNS Records to Hijack CDC, Corporate Domains for Malware Delivery
A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including Amazon S3 buckets and Microsoft Azure endpoints, by leveraging misconfigurations in the Domain Name System (DNS) records.
EXPLOITATION
5/20/20255 min read
Introduction to Hazy Hawk and Its Tactics
Hazy Hawk is a prominent cyber-espionage group that has garnered attention for its advanced tactics and methodologies in executing cyberattacks. Established by individuals with a background in sophisticated hacking techniques, the group primarily operates in the realm of cyber espionage, exploiting vulnerabilities within both governmental and corporate networks. Their activities have led to significant security concerns across various sectors, particularly those involving sensitive data and critical infrastructure.
The operational methodology employed by Hazy Hawk often involves intricate planning and execution, characterized by a deep understanding of their targets. One of their defining strategies is the manipulation of DNS (Domain Name System) records. By hijacking legitimate domains through DNS exploitation, Hazy Hawk can redirect users to malicious sites, enabling the delivery of malware and the extraction of valuable information. This technique highlights the importance of DNS security and the implications of its vulnerabilities.
As cyber tactics continue to evolve, understanding the operational strategies of groups like Hazy Hawk becomes crucial for enhancing defenses against such threats. The focus on DNS record exploitation serves as a reminder that cybersecurity is a dynamic field, necessitating ongoing vigilance and adaptation to stay ahead of cyber adversaries.
Understanding DNS Records and Their Vulnerabilities
The Domain Name System (DNS) is a fundamental component of the internet architecture, serving as a distributed database that translates user-friendly domain names into IP addresses. This conversion enables browsers to locate and connect to websites efficiently. DNS records are vital for directing internet traffic, as they contain specific instructions that allow the system to navigate the online landscape effectively. Common types of DNS records include A records, MX records, and CNAME records, each serving distinct purposes.
A records, or Address records, are essential for mapping a domain to its corresponding IP address, playing a crucial role in directing users to the correct server where a website resides. MX records, or Mail Exchange records, specify the mail server responsible for receiving emails on behalf of a domain, which is critical for email communication. CNAME records, or Canonical Name records, permit the redirection of one domain name to another, facilitating the use of various domain aliases that point to a single IP address.
Case Study: Hijacking of CDC and Corporate Domains
The emergence of Hazy Hawk as a prominent cyber threat actor has been marked by several notable instances of DNS record hijacking, particularly targeting high-profile organizations such as the Centers for Disease Control and Prevention (CDC) and various corporate domains. Through a sophisticated approach, Hazy Hawk has leveraged vulnerabilities within DNS configurations, allowing for the redirection of users to malicious sites under the guise of legitimate entities.
One significant case involved the CDC, where Hazy Hawk manipulated DNS records associated with the organization's domain. This sophisticated attack was executed through the exploitation of a misconfigured DNS setup, enabling the actor to redirect legitimate web traffic to a phishing site designed to harvest sensitive information from users. Following the hijacking, the impact was felt widely, with numerous unsuspecting individuals falling victim to the malware delivered via these compromised CDC domains. The incident raised significant alarms, prompting a rapid response from both the CDC and cybersecurity experts striving to mitigate further risks.
Similarly, various corporate entities have also been targeted by Hazy Hawk, with the hijacking of domains leading to substantial financial and reputational damage. In one such case, a major corporation faced an attack that exploited DNS vulnerabilities, leading to the dissemination of malware that compromised internal systems. The swift response from the targeted organization included a comprehensive forensic investigation and the implementation of enhanced security measures, which were crucial in preventing future breaches.
The scale and implications of Hazy Hawk's activities underline the critical need for robust DNS security practices. As organizations become increasingly aware of these threats, it is essential for them to adopt proactive strategies that include regular audits of DNS records and awareness training for employees. This case study underscores how easily established domains can be exploited, making the case for continuous vigilance in cybersecurity efforts.
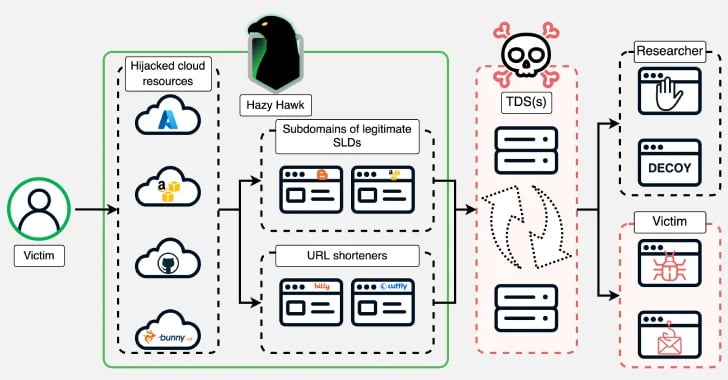
A threat actor known as Hazy Hawk has been observed hijacking abandoned cloud resources of high-profile organizations, including Amazon S3 buckets and Microsoft Azure endpoints, by leveraging misconfigurations in the Domain Name System (DNS) records.
The hijacked domains are then used to host URLs that direct users to scams and malware via traffic distribution systems (TDSes), according to Infoblox. Some of the other resources usurped by the threat actor include those hosted on Akamai, Bunny CDN, Cloudflare CDN, GitHub, and Netlify.
The DNS threat intelligence firm said it first discovered the threat actor after it gained control of several sub-domains associated with the U.S. Center for Disease Control (CDC) in February 2025.
It has since been determined that other government agencies across the globe, prominent universities, and international corporations such as Deloitte, PricewaterhouseCoopers, and Ernst & Young have been victimized by the same threat actor since at least December 2023.
What makes Hazy Hawk's operations noteworthy is the hijacking of trusted and reputable domains belonging to legitimate organizations, thus boosting their credibility in search results when they are being used to serve malicious and spammy content. But even more concerningly, the approach enables the threat actors to bypass detection.
Underpinning the operation is the ability of the attackers to seize control of abandoned domains with dangling DNS CNAME records, a technique previously exposed by Guardio in early 2024 as being exploited by bad actors for spam proliferation and click monetization. All a threat actor needs to do is register the missing resource to hijack the domain.
"Hazy Hawk is one of the dozens of threat actors we track within the advertising affiliate world," the company said. "Threat actors who belong to affiliate advertising programs drive users into tailored malicious content and are incentivized to include requests to allow push notifications from 'websites' along the redirection path."
In doing so, the idea is to flood a victim's device with push notifications and deliver an endless torrent of malicious content, with each notification leading to different scams, scareware, and fake surveys, and accompanied by requests to allow more push notifications.
To prevent and protect against Hazy Hawk activities, domain owners are recommended to remove a DNS CNAME record as soon as a resource is shut down. End users, on the other hand, are advised to deny notification requests from websites they don't know.
"While operators like Hazy Hawk are responsible for the initial lure, the user who clicks is led into a labyrinth of sketchy and outright malicious adtech. The fact that Hazy Hawk puts considerable effort into locating vulnerable domains and then using them for scam operations shows that these advertising affiliate programs are successful enough to pay well," Infoblox said.
Defensive Measures and Best Practices for Organizations
To mitigate the risks posed by DNS hijacking, organizations must adopt a multifaceted approach that emphasizes security, awareness, and proactive measures. One of the primary strategies involves securing DNS records. Organizations should employ registry locking features and regularly audit DNS settings to ensure unauthorized changes are detected promptly. Implementing DNSSEC (Domain Name System Security Extensions) can help in validating the authenticity of DNS responses, thereby preventing attackers from redirecting traffic to malicious sites.
Another essential practice is the adoption of multi-factor authentication (MFA). By requiring multiple forms of verification, organizations can significantly reduce the chances of unauthorized access to critical systems. This is particularly important for administrative accounts that have the ability to modify DNS records or other sensitive settings. Employees should be educated on the importance of strong, unique passwords and the role they play in maintaining the overall security of the organization.
Regular security audits are crucial in identifying vulnerabilities within an organization’s network. These audits should assess both technical controls, such as firewalls and intrusion detection systems, and organizational policies. Conducting penetration testing can help uncover potential weaknesses that could be exploited by threat actors like Hazy Hawk. In addition, organizations should remain vigilant by staying abreast of the latest security threats and trends in cyber warfare.
Finally, fostering a culture of cybersecurity awareness is vital for any organization. Training programs should be implemented to educate employees on recognizing phishing attempts, the importance of reporting suspicious activities, and following established security protocols. By raising awareness and promoting best practices, organizations can create a more secure environment that minimizes the likelihood of successful attacks.
In conclusion, a combination of securing DNS records, utilizing multi-factor authentication, conducting regular audits, and fostering cybersecurity awareness among employees can significantly enhance an organization’s defense against potential exploits by malicious groups like Hazy Hawk.
Source: https://thehackernews.com/2025/05/hazy-hawk-exploits-dns-records-to.html
